
How to Protect Your Network by Dropping Incoming ICMP Echo Requests to Device WAN Address
Introduction
In the vast tapestry of the digital world, our devices are constantly bombarded with a barrage of data packets, each vying for attention like boisterous voices at a bustling market. Among these, one type stands out: the ICMP Echo Request, also known as a ping. Like a relentless drummer at our network’s door, these requests seek to establish a connection and gauge the device’s presence and responsiveness. However, this seemingly innocuous communication can sometimes mask malicious intent, making it crucial to understand how to mitigate potential risks.
Defining ICMP Echo Requests and Their Significance
ICMP Echo Requests, or pings, are an essential tool in the network administrator’s toolbox. They serve as a diagnostic measure, allowing us to check if a particular device is online, measure latency, and identify network connectivity issues. By sending an echo request to a device, we can determine if it is reachable and assess the time it takes for the request to be sent and received. This information can be invaluable for troubleshooting network performance and ensuring smooth communication.
Potential Security Risks of Unrestricted ICMP Echo Requests
While ICMP Echo Requests can be beneficial for network management, unrestricted access to these requests can open doors to potential security threats. Malicious actors may leverage these requests to launch Denial-of-Service (DoS) attacks, flooding the target device with excessive pings, thereby overwhelming its resources and rendering it inaccessible. Additionally, attackers may utilize Echo Requests for reconnaissance purposes, probing the network for vulnerable systems and identifying potential entry points for further exploitation.
Configuring Firewalls to Drop Incoming ICMP Echo Requests to the WAN Address
To safeguard against these threats, it is imperative to configure firewalls to drop incoming ICMP Echo Requests to the device’s WAN address. This action blocks unauthorized external access to the network, significantly reducing the risk of DoS attacks and reconnaissance efforts. By limiting ICMP Echo Requests to trusted sources within the network, we can enhance network security without compromising essential diagnostic capabilities.
Step-by-Step Firewall Configuration Guide
-
Access the firewall configuration interface. This can typically be done through a web-based portal or command-line interface (CLI).
-
Create a new firewall rule that targets incoming traffic on the WAN interface.
-
Set the protocol to ICMP and the protocol type to ICMP Echo Request (Type 8).
-
Specify the source address as any or the desired range of IP addresses to be blocked.
-
Configure the action to “drop,” which will discard the incoming ICMP Echo Request packets.
-
Save and apply the firewall rule to activate the configuration.
Troubleshooting Firewall Configuration Issues
If you encounter issues after implementing the firewall configuration, consider the following troubleshooting steps:
-
Verify that the firewall rule is correctly configured and applied.
-
Ensure that the firewall is running and active.
-
Check the firewall logs for any relevant error messages.
-
Test the firewall configuration by sending an ICMP Echo Request from an external source.
Best Practices for Enhanced Network Security
In addition to configuring firewalls, consider employing the following best practices to further enhance network security:
-
Regularly update firmware and software to patch security vulnerabilities.
-
Monitor network traffic for unusual patterns or suspicious activity.
-
Implement intrusion detection and prevention systems (IDS/IPS) for real-time threat detection and mitigation.
-
Educate users on network security best practices, such as strong password management and avoiding suspicious emails or attachments.
Conclusion
Protecting your network from incoming ICMP Echo Requests to the WAN address is a crucial aspect of maintaining a secure network infrastructure. By implementing the firewall configuration outlined in this article and adopting best security practices, you can effectively mitigate the risks associated with unrestricted ICMP Echo Requests, safeguarding your devices and data from potential threats.
Call to Action
Are you interested in implementing these measures to enhance your network security? Share your experiences or ask any questions in the comments below, and let’s work together towards a safer digital future.
Image: www.thomasmaurer.ch
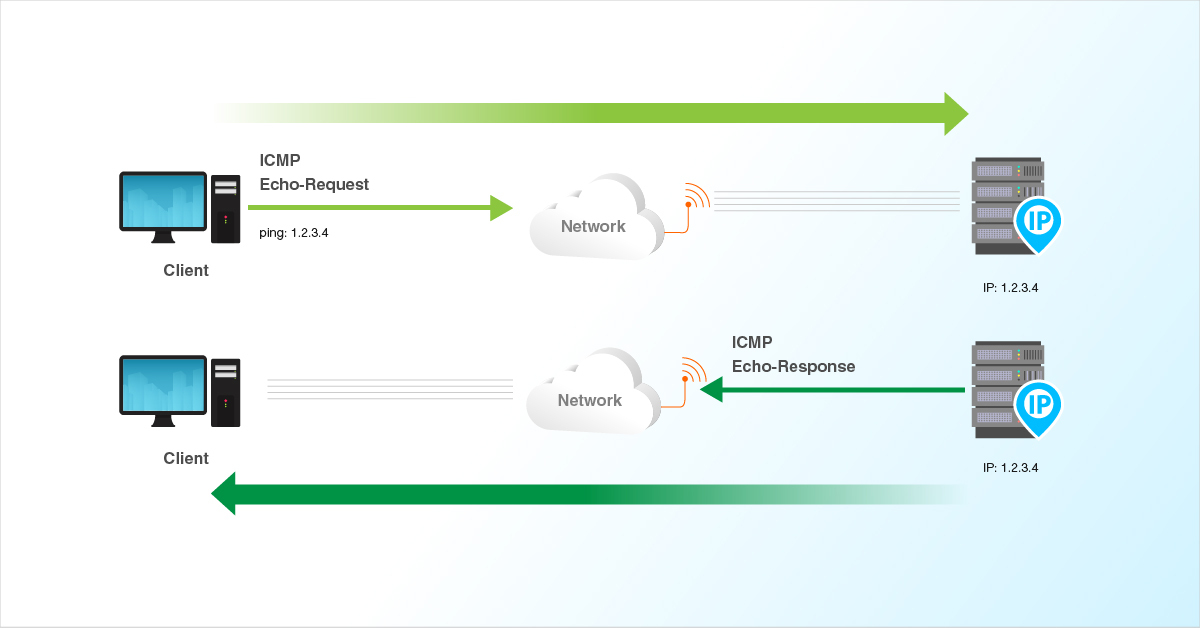
Image: www.layerstack.com
Ping tool in RouterOS In you need to apply the ACL on WAN interface in direction. It will block all the icmp echo request or replay coming to WAN interface will be block. (Either icmp replay going toward LAN users) If you want to allow the LAN users can ping outside but nobody can reach your network via ping (consider you are using 192.168.1./24 subnet as a LAN user.)